#kksctf open 2019 Write Up
This write up is a culmination of articles from a Capture The Flag competition and are all being concatenated here.
Red XOXOXO

The Challenge
We receive a message that is captured, and since this challenge is listed as “crypto”, we need to decipher the cipher text of -;91~.,11=12~;-?<27–6;:r~+-;~=27;0~1~=100;=p~7y3~)?7709~81,~+,~,;.2’p~55-%?*j=5.?.:j)0#*
 Our challenge information
Our challenge information
The Solution
The above cipher text has a variety of characters in it. Due to this, we can greatly reduce the type of encryption being used. Our hint also gives us a pointer in the right direction with the XOXOXO (XOR) in the title.
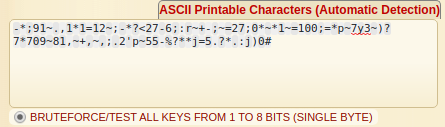 Brute forcing the key space
Brute forcing the key space
When attempting a variety of ciphers, a XOR brute force attack is attempted.
 Finding a possible key
Finding a possible key
Our brute force attack has found a possible key and provided us with positive confirmation in the form of clear text. Unfortunately, this is not the correct flag, as this tool and key combination do not give us correct output. Using another tool, we can brute force the key space and find the correct key.
 Finding the flag for the win
Finding the flag for the win
The key of 5e is found and the string is decrypted, revealing to us the final flag.
Stego Warmup

The Challenge
We get some file. Can you find secret?
We are provided the above file of Shaq gracefully obfuscating himself behind a tree. No other clues or hints are provided.
The Solution
This was an extremely easy steganography challenge. The flag we are looking for is embedded inside the image data. We can extract the EXIF metadata from the image using exiftool, revealing the final flag.
 Solved!
Solved!
We can see in the above image that the flag was in the Author field in clear text. On to the next challenge!
Xmas Tree

The Challenge
Do you like to decorate the Christmas tree?
This challenge was listed as “Misc”, and no other hints were provided.
The Solution
This was an easy challenge, as the answer was literally staring participants in the face during the entire CTF. Navigating to the kksctf web page showed a variety of Christmas themes, including a neat ASCII Christmas tree.
 ASCII Art!
ASCII Art!
The above tree ASCII art shows a few different pieces of text in different colors. If we look in the HTML source, we can see the **** tags which indicate a color change for certain pieces of text.
 It looks sweet in HTML too!
It looks sweet in HTML too!
Combining the 7 pieces of colored text results in the final flag of kks{n3w_y34r_m@dn3$$}. Happy New Year!
Postman

The Challenge
Hey, some haсkers steal my mail. Can you help return and deliver it?
The Postman challenge provides us with a remote website and port. Navigating to the site shows us only a single line of text asking us to help the user retrieve their email.
The Solution
Let’s help the user get their mail! Trying things like a mail. sub-domain unfortunately did not work. We will have to go back to basics. Checking the robots.txt file gives us an unlisted URL to check.
 robots.txt
robots.txt
We find the /postbox URL and navigate to it, but immediately get shut down due to an incorrect HTTP call.
 Denied
Denied
“Method Not Allowed” indicates that we made an incorrect type of request to the web server. By default, this call is a GET request. We can either change the request type using proxies or extensions in our browser, or we can use curl and send a POST request. While GET makes a call to retrieve information from a website, POST sends data (such as logging into a mailbox service!).
curl -X POST http://tasks.open.kksctf.ru:8001/postbox
 The final flag
The final flag
The request is processed and the final flag is returned to us. Our user is now happy that they have their mail, and we are happy that this challenge is solved.
Note This content was originally posted at https://medium.com/@forwardsecrecy/kksctf-open-2019-red-xoxoxo-df2b1fe454f2 and is being re-hosted here for archival purposes.
